Table of Contents
What is Bitlocker
BitLocker Drive Encryption is a data protection feature that integrates with the operating system and addresses the threats of data theft or exposure from lost, stolen, or inappropriately decommissioned computers.
BitLocker provides the most protection when used with a Trusted Platform Module (TPM) version 1.2 or later. It works with BitLocker to help protect user data and to ensure that a computer has not been tampered with while the system was offline. You can still use BitLocker on systems without a TPM device, however, this implementation will require the user to insert a USB startup key to start the computer or resume from hibernation.
The current version of Windows 10 (1909) includes BitLocker's latest features:
- XTS-AES encryption algorithm. BitLocker now supports the XTS-AES encryption algorithm. XTS-AES provides additional protection from a class of attacks on encryption that rely on manipulating cipher text to cause predictable changes in plain text. BitLocker supports both 128-bit and 256-bit XTS-AES keys.
- Credential Manager support. Credentials that are stored with Credential Manager, including domain credentials, are protected with Credential Guard
Bitlocker Requirements
For BitLocker to use the system integrity check provided by a Trusted Platform Module (TPM), the computer must have TPM 1.2 or later. If your computer does not have a TPM, enabling BitLocker requires that you save a startup key on a removable device, such as a USB flash drive.
A computer with a TPM must also have a Trusted Computing Group (TCG)-compliant BIOS or UEFI firmware. The BIOS or UEFI firmware establishes a chain of trust for the pre-operating system startup, and it must include support for TCG-specified Static Root of Trust Measurement. A computer without a TPM does not require TCG-compliant firmware.
The system BIOS or UEFI firmware (for TPM and non-TPM computers) must support the USB mass storage device class.
The hard disk must be partitioned with at least two 'drives':
- The operating system drive (or boot drive) contains the operating system and its support files. It must be formatted with the NTFS file system.
- The system drive contains the files that are needed to load Windows after the firmware has prepared the system hardware. BitLocker is not enabled on this drive. For BitLocker to work, the system drive must not be encrypted, must differ from the operating system drive, and must be formatted with the FAT32 file system on computers that use UEFI-based firmware or with the NTFS file system on computers that use BIOS firmware. This will happen automatically in most cases.
When installed on a new computer, Windows will automatically create the partitions that are required for BitLocker.
Use cases
Data on a lost or stolen computer is vulnerable to unauthorized access, either by running a software-attack tool against it or by transferring the computer's hard disk to a different computer. BitLocker helps mitigate unauthorized data access by enhancing file and system protections. BitLocker also helps render data inaccessible when BitLocker-protected computers are decommissioned or recycled.
How to enable BitLocker
These instructions apply to a system without a TPM
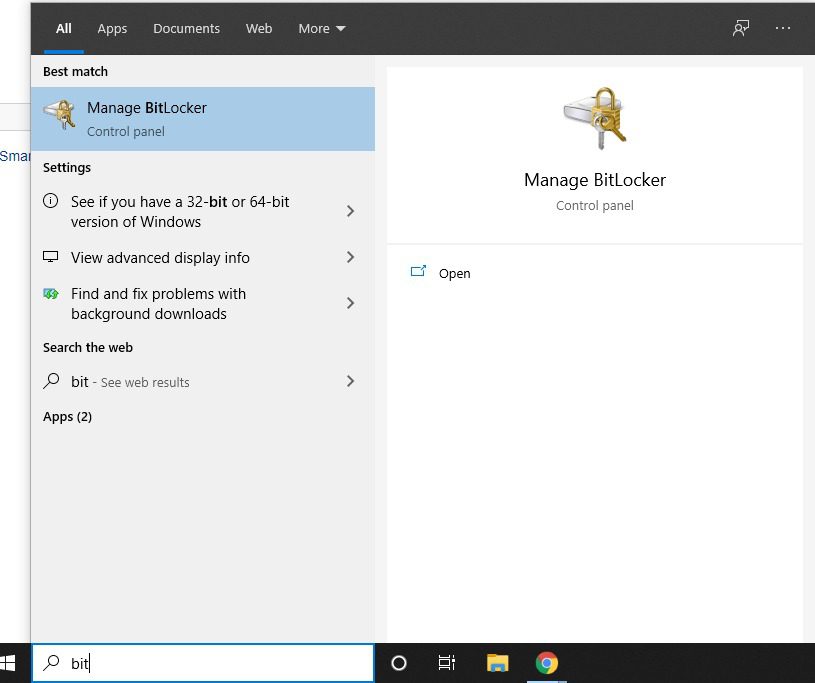
1. Click the Start button and type BitLocker
2. Select Manage BitLocker
3. Locate the drive you wish to encrypt and select Turn on BitLocker
4. Choose how you want to unlock this drive. Most likely you will select Use a password to unlock the drive
5. Choose where you would like to backup your memory key. This is where the USB comes in.
6. Select the USB device you would like to use
Now you will choose how much of the drive you wish to encrypt and this is entirely up to you. Read through the tooltip carefully then make your choice.
You will be prompted to select an Encryption Mode. We recommend utilizing XTS-AES (New encryption mode) is this is the most secure. If you are performing this action on an external or other device that may be transferred to another system and back, the Compatible mode might be your best option.
It's time to encrypt your device.
7. Select Start encrypting
Depending on the type and size of drive, which encryption methods you chose and other environmental factors, this process can take a significant amount of time.
Conclusion
BitLocker provides an exceptionally secure and simple way to encrypt your storage devices. Following through this guidance will allow you to encrypt your storage devices correctly and efficiently.
Troubleshooting
A common issue is your encryption not being 'allowed' by group policy.
You can bypass this limitation through a Group Policy change. If your PC is joined to a business or school domain, you can’t change the Group Policy setting yourself. Group policy is configured centrally by your network administrator.
If you’re just doing this on your own PC and it isn’t joined to a domain, you can use the Local Group Policy Editor to change the setting for your own PC.
1. Select the Start button, type gpedit.msc
2. Navigate to Local Computer Policy > Computer Configuration > Administrative Templates > Windows Components > BitLocker Drive Encryption > Operating System Drives in the left pane
3. Select the Require additional authentication at startup option in the right pane
4. Select Enabled at the top of the window, and ensure the Allow BitLocker without a compatible TPM (requires a password or a startup key on a USB flash drive) checkbox is enabled
5. Click OK to save your changes. You can now close the Group Policy Editor window.
Your change takes effect immediately, you don’t even need to reboot!
Need help with your Puget Systems PC?
If something is wrong with your Puget Systems PC. We are readily accessible, and our support team comes from a wide range of technological backgrounds to better assist you!
Looking for more support guides?
If you are looking for a solution to a problem you are having with your PC, we also have a number of other support guides that may be able to assist you with other issues.